Cybercrime
The misuse of achievements in the field of information and communication technology is a security threat which will be more and more prominent and which will serve as the basis for numerous forms of organized criminal activity.
The contemporary development of information and communication technology (ICT) and its increasing presence in all spheres of the society have led to an increase in the number of cybercrime offenses.
The fact that more and more people use social media, mobile platforms and apps is certainly one of the main reasons for the increase of this particular type of crime.
According to estimates, social networking sites will reach record-breaking 3.96 billion users in 2023, and this number will continue to grow as the use of mobile devices and social media starts to increase on the markets that were previously underdeveloped in this respect.
The quantity of data and the intensity of online communication has been growing rapidly from one year to another.
According to statistics of the YouTube, about three hundred hours of videos are uploaded and 3.67 million videos are viewed, while 167 million videos are viewed on TikTok platform every minute.
In the same amount of time, 321 million emails are sent, and six million people engage in online purchase.
Facebook has about 2.1 billion active users and 83 million fake accounts.

The development of IT, digital technology and accompanying technical achievements, as well as the increase in the number of their users, have rapidly accelerated in our country, which can be seen, inter alia, from the fact that 85.4% of the population uses the internet, and that as many as 82.3% of citizens have accounts on some of the social media. This generally positive process is also a powerful generator of cybercrime and similar crimes, i.e., those the commission of which has been made possible as a result of the application of ICT. In most cases, perpetrators do not really understand that certain actions constitute a crime, but they also mistakenly believe that IT protects them from being identified. Also, they frequently misunderstand their civil rights and freedoms, especially those that pertain to the public expression of views. In addition to this, cybercrime carries special challenges in the form of the increasingly frequent (mis)use of cryptocurrencies, anonymous communication through VPN servers and the TOR network, increase in criminal offenses through ransomware attacks, as well as further development of artificial intelligence.
Present Forms of Cybercrime
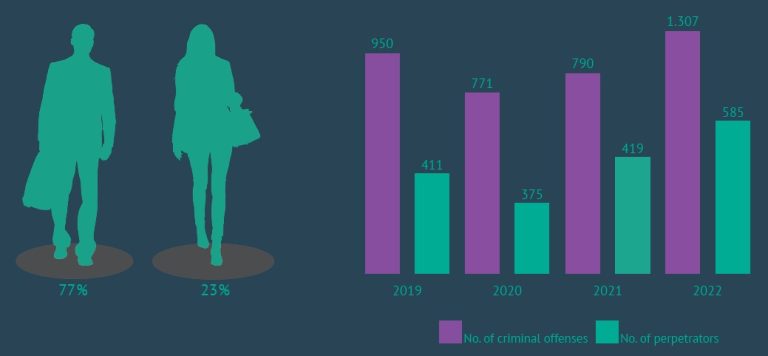
According to the Special Prosecutor’s Office for Cybercrime of the Republic of Serbia, the most frequently committed cybercrime offenses in the last four years were: endangerment of safety, showing, procuring and possessing pornographic material and exploiting a minor for pornography and fraud, and they were followed by unauthorized access to a protected computer, computer network or electronic data processing and computer fraud. The number of reported criminal offenses of endangerment of safety and fraud has increased, while the reporting of criminal offenses of computer fraud and unauthorized access to a protected computer, computer network or electronic data processing is in a slight decline. The number of persons against whom criminal reports have been filed is growing exponentially, and the same applies to the number of reports for stalking and sexual harassment, where the victims are mostly women. The internet is suitable for the commission of these crimes because it makes it possible for perpetrators to remain anonymous. In this context, it is necessary, inter alia, to raise people’s awareness of the criminality of such behavior, both in person and online, in order to encourage victims to report the perpetrators and participate in criminal proceedings.
The number of cybercrime offenses detected by the Ministry of Interior of the RS has significantly increased, by more than 1,000 in the period between 2019 and 2022 compared to the previous four-year period. Also, the number of detected crimes was by 38% higher in 2022 compared to 2019, which is just another indicator of the expansion of this type of crime.
Online sexual exploitation of children is one of the most serious forms of cybercrime and it is manifested in exactly the same way as in the previous years, but children’s access to digital devices and contents is now greater, which is particularly conducive to crimes in which they are sexually exploited. These crimes are committed through social media and with the aid of software programs that function as closed Peer-to-Peer networks, where juvenile pornography contents are accessed and photographs and video materials are obtained from the places they are stored at, such as DropBox and 4Shared online storage and hard drives. It was observed that pornography is mostly collected through the Peer-to-Peer program Shareza, through social media, such as Facebook, Instagram, TikTok, Vkontakte, Gnutella, and through communication apps, such as Viber, WhatsApp, Telegram, etc.
Lately, the sexual harassment of children through social media, mobile apps and other available services has become more prominent. It is in the shape of inappropriate messages and calls with sexual connotation, playing of pornographic content and contacts from fake accounts for the purpose of engaging in closer communication within which minors sent explicit contents and are then forced to continue doing it.
The Ministry of Interior has intensified activities aimed at suppressing the online sexual exploitation of children and has launched a special operation named Armageddon. Since the beginning of the operation, or more precisely between 2010 and October 2023, a total of 565 criminal reports were filed against a total of 493 persons for the commission of 780 criminal offenses against sexual freedom in which minors were victimized and criminal offenses against freedoms and rights of man and citizen. Reports received through international police cooperation, Interpol, Europol, FBI, Homeland Security Investigation, etc. are also actively dealt with.
A new trend has been observed over the past four years, and that is a more frequent commission of the criminal offense of unauthorized use of copyrighted work or other work protected by similar right. This mostly refers to unauthorized recording and copying of films and television series and their posting on social media.
When we compare the aforementioned data with the findings from Europol’s 2022 Internet Organised Crime Threat Assessment (IOCTA 2022, updated in February 2023), we can see that some trends in our country match those in the European Union and the world. Namely, IOCTA points to main trends in criminal offenses in 2022, which include criminal offenses related to cybercrimes, online sexual exploitation of minors and different types of online fraud through the misuse of credit cards and data pertaining to cash and financial accounts.
Within the criminal offenses against security of computer data, we can single out the criminal offense of unauthorized access to computer, computer network or electronic data processing, which accounts for nearly 80% of the total number of these crimes. Followed by computer fraud with 12%.
It is dominant because some of its forms are directly related to other cybercrime offenses, but also to fraud, counterfeiting and abuse of credit and debit cards, ransomware attacks, etc. As for computer fraud, one of its frequent forms of commission is unauthorized access to email servers with the aim of redirecting emails or creating phishing campaigns with the ultimate goal of getting funds held at citizens’ current accounts.
In one of the cases of computer fraud, payment instructions sent to a foreign supplier were intercepted. The company suffered damage after it was misled into paying hundreds of thousands of euros to the account of an unauthorized recipient in two individual transactions.
Also present are the criminal offenses of counterfeiting and abusing credit and debit cards, which are committed either on their own or concurrently with the criminal offense of fraud. Most frequently, fake pages are created on social media on which posts on cash donations are created, which is how perpetrators get data about citizens’ credit and debit cards and take money from their accounts.
Online illicit trade in pharmaceuticals is also present, where pharmaceuticals are delivered to customers through a courier service. There are also frauds in the form of non-delivery of purchased goods, offers of false employment aboroad through various gifts, etc.
Digital violence is almost a constant companion of the virtual space, so the number of reported criminal offenses of endangerment of safety is still high. They are mostly carried out through social media, and in a number of them, threatening messages were sent to some public officials. Past two years were marked by a specific form of digital violence aimed at causing panic and disorder – perpetrators emailed disinformation and false anonymous reports alleging that explosive devices were placed in numerous educational, commercial and business facilities.
The COVID-19 pandemic led to the appearance of new crimes in this area, so that this period was frequently marked by the criminal offense of causing panic and disorder through the spreading of fake news and claims on social media, which significantly hindered the implementation of state authorities’ decisions and measures aimed at fighting COVID-19. Undoubtedly, the most frequent crime was the forging of vaccination certificates and negative PCR test. One case of forging of documents was recorded, i.e., of issuing forged vaccination certificates and a negative PCR test, through the use of online data of the Business Registers Agency. The perpetrator created and registered an internet domain whose name was almost identical to that of eUprava (e-Administration), and used it as the server for a database of forged negative covid test certificates. When the QR code was scanned, a forged certificate was obtained, identical to the original one, which fooled those who checked the validity of the certificates due to the great similarity of the domain names.
In the field of cybercrime, there are two other topical types whose main goal is to attack computer networks and systems. These are ransomware attacks and abuse of virtual currencies (cryptocurrencies).

Ransomware attacks are a global phenomenon and are only financially motivated.
Attackers use malicious computer programs to extort money from victims (usually private companies or public institutions, rarely individuals). In most recorded cases, victims’ computer systems were not well protected, and the attackers succeeded in accessing their business databases and locking (encrypting) data files. Then, in exchange for the file decryption key, they demanded ransom from the victims, in virtual currencies only (mainly Bitcoin and Monero).
Attackers most frequently use social engineering, impersonation and phishing techniques for such attacks. Victims frequently do not know enough about information technology, due to their carelessness, they let a malicious program be installed on their computer system. The installation of such programs is also frequently caused by technical failures in operating systems or computer protection.
A new aspect of these attacks is that payment instructions are frequently sent only once the victim contacts the attacker, as opposed to earlier, when they arrived together with the information about the attack. The attacker’s contact address is linked to a service that uses darknet servers, where a high level of anonymity is secured. The price of unlocking depends on the importance of the data and the size of the attacked company or institution (if the victim is “important” or has important data, the amounts are higher). Another novelty is the exploitation of data before locking. After breaking into the system, the attackers copy the data to their servers, and then threaten the victim that they will sell them on the darknet if the required amount is not paid. Ransomware attacks are also increasingly frequent – the attacker does not write the malicious code, but buys it on the darknet and runs it once he accesses the victim’s server. After the attack, part of the profit (10-20%) is given to the code developer.
In recent years, cryptocurrency abuse has become more prominent, since this type of digital assets has attracted much attention as the object of investment and potential source of profit.
As early as in 2014, the National Bank of Serbia issued a warning saying that Bitcoin was not a legal tender in Serbia and that, due to the fact that no legal protection existed in this field, investments in Bitcoin or similar virtual currencies, which the central bank did not issue or guarantee their value, represented a risk and might cause financial losses. A few years later, in mid-2021, the Law on Digital Assets entered into force, regulating this area and defining requirements for business entities wishing to engage in cryptocurrency exchange activities. In late 2022, two exchange offices were licensed by the National Bank of Serbia for these activities.
Below are the most common types of cryptocurrency abuse:
Cryptocurrency Theft
The attacker installs malware on the victim’s computer in order to steal private keys, and then transfers cryptocurrencies to addresses under his control.
The attacker sends phishing links in order to take over cold and hot (online exchange) wallets, and then transfers cryptocurrencies to addresses under his control.
Cryptocurrency Fraud
Ponzi scheme – investing cryptocurrencies in “projects” which initially bring profit, but once the number of participants increases, they stop working, while investors are defrauded and lose the invested amounts.
Scams through fake online campaigns for financial gain, which are used for phishing in order to get unauthorized access to citizens’ current accounts. Perpetrators pay funds from these accounts to cryptocurrency sellers (on special platforms), who then transfer the agreed amount (also in cryptocurrency) to their wallet addresses. Investment frauds, which represents an organized type of fraud. Call centers are organized in a country and are used for defrauding victims in other countries. Fake websites that allegedly offer investments in new cryptocurrencies are created, while victims are targeted through social media. After that, the contact is transferred to rented VoiP phone numbers, making the victim believe he/she is talking to someone from his/her own country (call centers employ people who are fluent in the victim’s language). After that, the victim is led to invest in cryptocurrencies, and the investment amounts increase over time. When the victim requests to withdraw what he/she has earned, he/she is denied access and the platform is shut down. The paid cryptocurrencies are transferred to the wallet addresses controlled by the perpetrators.
DDoS Extortion (Attacks)
Distributed denial of service (DDoS) is a method of attack on private and public business entities. Such attacks are not only financially motivated but also launched for ideological, political or purely malicious reasons. They are becoming increasingly easier and cheaper, while the risk of detection is relatively low. In case of a financially motivated attack, businesses and other entities are requested to make a payment in cryptocurrency to stop being targeted by such attacks in future.
Money Laundering Through Cryptocurrency
Money laundering is one of the key stages of cryptocurrency crime. Its goal is to conceal the origin of cryptocurrencies, to exchange them for an official, fiat currency, and then to transfer them into legal flows.
The anonymity of cryptocurrency transaction participants (unlike the transactions themselves) has given momentum to money laundering through cryptocurrency. The Cybercrime Suppression Service at the Ministry of Interior has developed a typology of this method of money laundering, which includes the following types: use of private coins, use of mixers (centralized and decentralized CoinJoin services), exchanging one cryptocurrency for another (centralized), use of decentralized exchanges, use of online casinos, use of peer-to-peer services and cryptocurrency ATMs, use of mining pool and, as a separate type, a combination of all the above.
Factors that favor cybercrime and future challenges:

Digitization of social processes - The digitization of an increasing number of areas of social life and processes, including online banking, social media, e-commerce, health care, communications, etc., makes cybercrime attacks more possible; Profitability - Cybercrime can be very profitable, frequently even more profitable than conventional types of crime; Lack of security awareness – Most people who use modern digital technology are completely unaware of the underlying security risks and dangers, and are therefore very vulnerable to all forms of cybercrime;

Global connectivity - Digital technology enables global action, which creates numerous challenges regarding the identification of perpetrators of cybercrime; Legal and legislative challenges - A lack of uniform legislation on user data storage and information sharing in Europe hampers the prosecution of perpetrators and international criminal investigations; efficient cybercrime investigations and prosecution call for continuous international cooperation, primarily of law enforcement agencies, because cybercrime perpetrators should be identified throughout the world almost every day and electronic evidence of their crimes should be investigated and secured;

Anonymity enabled by further IT development - In addition to the already mentioned tools, such as the VPN and TOR network, IP addresses provided by Carrier-Grade NAT (GNAT) represent a special problem, because they are stored by internet providers and frequently do not allow unequivocal user identification; cryptocurrencies, as relatively simple and anonymous tools for money laundering, collection of ransom or payment for illegal services, are another example.
A number of persons were arrested in 2021 and 2022 on suspicion that they had misrepresented cryptocurrency trading and misled victims into investing money. They used the following platforms: grandpacifictride.com, coinwealthinv.com, ashfordcapitallnv.com, victoria-coins.com, royaloakinvestment.com, aurora-coins.com, stockscm.com, financialcentre.com, richmondsuper.com, investmentsglobal.com and gatebits.com, and the victims were citizens of Australia, New Zealand, Sweden, Canada, Japan, Switzerland and Germany. They used global VoIP technology for connecting and communicating with them.
Expected Future developments
► Artificial intelligence (AI) and machine learning technologies have advanced significantly in the recent years, and their accessibility and implementation are greater than ever. A special challenge will be chatbots, AI-based software that simulates human conversation (they are also called virtual assistants or chat agents). AI can be used differently for criminal purposes. It can be an instrumentality as well as a tool for predicting the behavior of individuals or legal entities and identifying and exploiting their vulnerabilities. One of its possibilities of particular concern is deepfake, which represents the generation of fake content through the manipulation of video and sound. AI can also be used for finding out access codes, impersonation on social media, concealing malware (resulting in potential system breaches), hacking and numerous other types of abuse, which will spread on an unprecedented scale parallel with its development. This is supported by the fact that software programs for this technology are becoming more and more accessible, and those who master them also gain greater opportunities for launching cyber-attacks.
► We can expect that the use of end-to-end encryption in communication among participants in different criminal activities will continue, since encrypted communication platforms represent one of the most effective ways for maintaining anonymity of conversations or content sharing, or for making wiretapping difficult.
► The emergence of highly sophisticated forms of cybercrime is also inevitable. This refers to the growth of the so-called APT (advanced persistent threat) attacks, which are launched by groups whose presence on networks is frequently detected only after several months, or even years. Their goals are the exfiltration of data, cyber espionage, ransomware attacks, etc.
► We should also take into account the great IT expertise of certain participants in this field, who are ready to sell their “services” for profit, regardless of the far-reaching and unpredictable consequences.


